Dahua Easy Installation Simple, Quick and User-friendly Installation, Installation is a significant part of any monitoring camera. It is something that installers need to carefully consider and think about before purchasing any equipment. The camera structures may affect the steps required to complete the task, the cost that can be incurred, the number of people needed, etc.
As a world-leading video-centric AIoT solution and service provider, Dahua has a lot in store for us in terms of making camera installation simple, quick and user-friendly. Its recently launched 5E initiative focuses on user-centered design and aims to provide customers with efficient operations, cost reduction, security guarantees, and value enhancement. Easy Installation, one of Dahua 5E’s key components, refers to easy hardware installation and easy software deployment. For hardware, Dahua constantly optimizes their structural design, tools requirements, guide materials, process safety, etc., so as to improve the hardware’s ease of installation. For software, Dahua continuously optimizes their accessibility, flexibility, complexity, and correctness, thus enhancing the easy installation of software products.
Here are some of the highlights of Dahua 5E’s Easy Installation:
Dahua PTZ
Pain Points:
Solutions:
Application Scenarios: retail store, villa
Dahua Easy Installation Manual v1
Also Read : DAHUA IP Camera 5.0 UI Setup
Dahua IPC
Pain Points:
Solutions:
Application Scenarios: cafe, parkland
Dahua ITC Cardan Bracket 8019
Pain Points:
Solutions:
Application Scenarios: highway, urban roads
HDCVI
Pain Points:
Solutions:
Application Scenarios:
What is Symmetric Encryption Algorithm?
In the modern stage of cryptography, the concept of key secrecy was introduced, giving rise to a new encryption algorithm paradigm called symmetric encryption algorithm.
Symmetric encryption algorithm, also known as single-key algorithm, is characterized by the use of an identical key for both encryption and decryption. They can be broadly classified into two major types: sequence ciphers (also known as stream ciphers) and block ciphers.
The core of stream cipher encryption is the key (also known as the seed key) that goes through a key stream generator to produce a key stream. This key stream is then XORed with the plaintext byte stream to obtain the ciphertext byte stream, encrypting one bit or one byte of the data stream at a time. The encryption process is illustrated in Figure 1.
Figure 1: Steam Cipher Encryption/Decryption Process
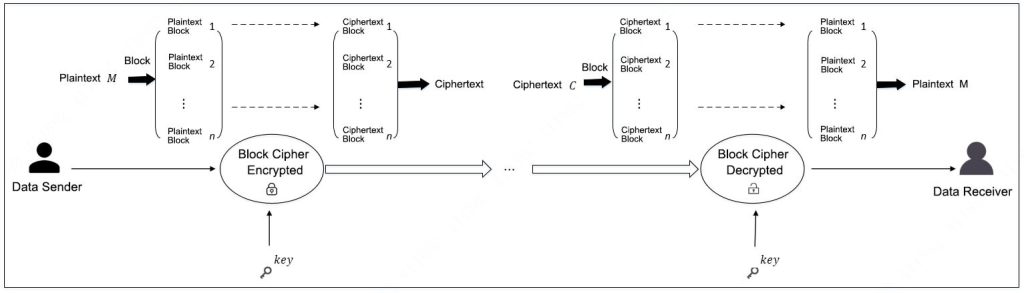
The core of block cipher encryption is to divide the plaintext data into fixed-length blocks and encrypt them using a key, resulting in ciphertext blocks. The plaintext is encrypted on a byte-by-byte basis. The process is illustrated in Figure 2.
Figure 2: Block Cipher Encryption/Decryption Process
Block cipher encryption is achieved by grouping the plaintext. To enhance the security in the encryption process and facilitate grouping, two key points are usually considered: encryption modes and padding modes. As for the specific selection of encryption mode or padding mode, it often depends on practical application scenarios, required security strength, and other factors.
The introduction of encryption modes mainly considers whether there should be any correlation between different blocks or whether each block should be encrypted independently. Different encryption modes represent different iteration methods used in the encryption process of plaintext blocks. Table 1 provides the advantages and disadvantages of using different encryption modes.
|
Encryption Mode |
Advantage |
Disadvantage |
Remarks |
|
CBC (Cipher Block Chaining) |
1. Repeated permutations of plaintext are not reflected in ciphertext 2. Decryption supports parallelism |
1. Encryption does not support parallelism 2. Error propagation in encryption |
Recommended |
|
OFB (Output FeedBack) |
1. Error propagation-free encryption and decryption 2. The encryption of the counter can be calculated in advance 3. The same plaintext block does not result in the same ciphertext block |
Non-support for parallel encryption and decryption |
Recommended |
|
CTR (CounTeR) |
1. Decryption and decryption support parallelism 2. Error propagation-free encryption and decryption 3. The encryption of the counter can be calculated in advance |
Difficult to guarantee the uniqueness of an IV |
Recommended |
|
GCM (Galois/Counter Mode) |
1. Integrity verification 2. Support for parallel computation in encryption and decryption |
More complex for encryption and decryption compared to other modes |
Recommended |
|
CFB (Cipher FeedBack) |
Decryption supports parallelism |
1. Non-parallel encryption 2. Error propagation in encryption 3. In decryption, an incorrect ciphertext can affect two plaintext results |
Not recommended |
|
ECB (Electronic CodeBook) |
1. Simple and easy implementation 2. Support for parallel encryption and decryption 3. Error propagation-free encryption and decryption |
1. Repeated permutations of plaintext are reflected in ciphertext 2. Easy to manipulate plaintext by tampering with ciphertext groups |
Not recommended |
Table 1: Comparison of Several Encryption Modes
The introduction of padding modes mainly addresses the issue of plaintext that is not a multiple of the specified block size. In such cases, the remaining bits need to be padded to match the algorithm’s specified block size. During encryption, the plaintext is padded, and during decryption, the padding needs to be removed according to the same padding mode. Table 2 presents several common padding methods in block ciphers.
|
Padding Mode |
Padding Method |
Remarks |
|
PKCS#7 Padding |
If a block represents a data unit of length n bytes, and the original plaintext length is not a multiple of n, padding is added to make it a multiple of n. The padding value used is the length of the padding itself. If the original plaintext length is already a multiple of n, an extra block is added with a padding length of n, and the padding content is set to the length of the padding. |
Recommended |
|
PKCS#5 Padding |
Similar to PKCS#7 Padding, but with a fixed block size of 8 bytes, the plaintext is padded to a multiple of 8 bytes. If the original plaintext length is n, the required padding length is 8-(n % 8), and the padding content is set to the length value of the padding. |
Recommended |
|
ISO 10126 Padding |
Padding is applied to make the data size a multiple of the block size. In this case, the last byte of the padding content represents the number of padding bytes added, while the other bytes are filled with random values. |
For CBC mode only |
|
No Padding |
No padding is used, and the plaintext must be a multiple of the specified block length. |
Not recommended |
|
Zeros Padding |
The plaintext is padded with zeros to make it a multiple of the specified block size. |
Not recommended |
Table 2: Comparison of Several Padding Methods
Symmetric encryption algorithms encompass various algorithms, such as RC4 and ZUC for stream ciphers, and DES, 3DES, and AES for block ciphers. They are mainly used to address issues related to secure transmission, secure storage, and have a wide range of applications. However, these algorithms also have drawbacks, such as difficulties in key distribution and the inability to provide non-repudiation, which restrict their application in certain scenarios.











Add Comment